Decrypt Keychain.plist
Download naruto shippuden sub indo. Naruto Shippuden Episode 496 Subtitle Indonesia – Ketemu lagi dengan kami Genesis team disitus download anime subtitle indonesia lengkap dengan berbagai macam genre anime ada disini dengan format video mp4, 3gp, 480p, 720p dan anime BD series. Kali ini kami akan posting anime On going 2007 Naruto Shippuden Subtitle Indonesia dengan genre Action, Comedy, Martial Arts,Shounen, Super Power. Manga ini kemudian diadaptasi menjadi sebuah anime televisi, yang diproduksi oleh Studio Pierrot dan Aniplex. Naruto Shippuden adalah serial manga Jepang yang ditulis dan diilustrasikan oleh Masashi Kishimoto.
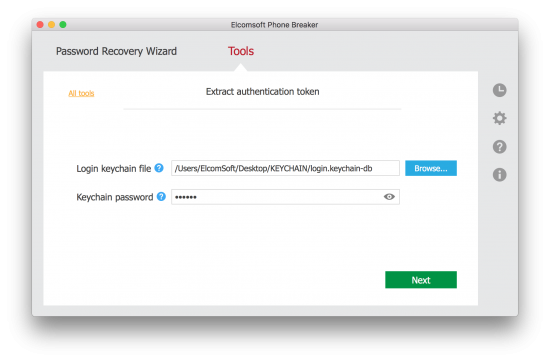
The video shows the usage of iOS keychain viewer which list out all the items from the keychain. For more details visit - http://www.securitylearn.net/2012/1. Keychain>Metro last light redux repack. This is the fully qualified path to the login.keychain of the user whose data you are This is the path (relative or absolute) to write the decrypted Form Values plist file.
I am using this code to encrypt but how do I check whether the data has been encrypted or not? Is it correct way to encrypt? NSData *data = [NSData dataWithContentsOfURL:[NSURL URLWithString:@'data.plist']]; NSError *error1; NSData *bac = [RNEncryptor encryptData:data withSettings:kRNCryptorAES256Settings password:@'abcdef' error:&error1]; NSString *pathToDesktop = [NSString stringWithFormat:@'/Users/rajparmar/Desktop/rajuencrypt.text']; [bac writeToFile:pathToDesktop atomically:YES]; – Mar 4 '15 at 11:02 •.
Last October, I participated as speaker at the SANS DFIR Summit in. It was a great meeting and I am very happy to have been able to participate. My speech was focused on DPAPI, the Windows Data Protection API, and how it could be used during a post-mortem digital investigation to access protected information: overcoming system's security it's sometimes necessary to access data otherwise not available. I like to call this 'process' ODI, Offensive Digital Investigations. I want to be brief, skipping any DPAPI introduction and only providing some links for readers who don't know what DPAPI might be. Consider simply the fact that the technology was introduced with Windows2000(!!) and you and/or your system/applications use it every day.
Moreover, if you wonder how wifi passwords are protected, how IE or Chrome treats saved credentials, how Dropbox encrypts its databases, how iCloud protects user credentials, how EFS ( Encrypting File System) gets unlocked and so how your private asymmetric key is safeguarded. Then you need to know what DPAPI is and how it works. You can download my slides ' Give Me the Password and I'll Rule the World' from and this is the links list: •, MSDN 2001 • DPAPI Secrets ( & ), Passcape 2012 •, BlackHat 2010 The last work is an awesome research made by Elie Bursztein and Jean-Michel Picod, who first published DPAPI intimate details. They even provided dpapick, an Open Source Python tool able to offline decrypt DPAPI blobs (aka the encrypted information) up to Windows Vista. Their work is a milestone to deeply understand this technology, and it was my entrance and reference when I started to dig inside DPAPI. For this reason I decided to try improving dpapick by adding Windows7 and Windows 8.1 support: after some nights inside WinDbg, I was able to decrypt blobs coming from these systems, just in time for the SANS conference.
Then Jean-Michel took my patch, refactored the code and added some other cool features, releasing the dpapick version 0.3 in the middle of October: check the new features added in his blog post. Just a note on Windows 8.1: DPAPI decryption is supported only for local accounts, not for online accounts. As you can read, ' [DPAPI is] used to encrypt and decrypt static data on a single computer. Cloud computing, however, often requires that content encrypted on one computer be decrypted on another': so Microsoft introduced DPAPI-NG to allow sharing of secrets/whatever on different computers, after proper authentication and authorization.
DPAPI-NG is used when working with online user accounts, and it's not currently supported by dpapick. Ideally this post should have been published few days after the meeting, anyway it's here: some examples on how you can use dpapick to access data protected by DPAPI tech.